It’s crucial to properly configure the security settings for qBittorrent’s web interface to prevent unauthorized access and potential security breaches. Default credentials and UPnP settings can pose significant risks, as demonstrated by a recent incident where an attacker exploited these vulnerabilities to install Monero mining software on a user’s PC. However, users can mitigate these dangers by following a few simple yet crucial steps.
Firstly, users should change the default credentials for accessing qBittorrent’s web interface. This involves creating a strong, unique password that is difficult for attackers to guess. Additionally, disabling UPnP (Universal Plug and Play) is recommended to prevent unauthorized devices from accessing the qBittorrent client.

Furthermore, enabling HTTPS encryption for the web interface adds an extra layer of security by encrypting data transmitted between the client and the user’s web browser. This helps protect sensitive information, such as login credentials, from being intercepted by malicious actors.
Regularly updating qBittorrent to the latest version is also essential, as developers frequently release security patches and updates to address newly discovered vulnerabilities and improve overall security.
By following these steps and staying vigilant about security best practices, users can significantly reduce the risk of unauthorized access and potential security threats when using qBittorrent’s web interface.
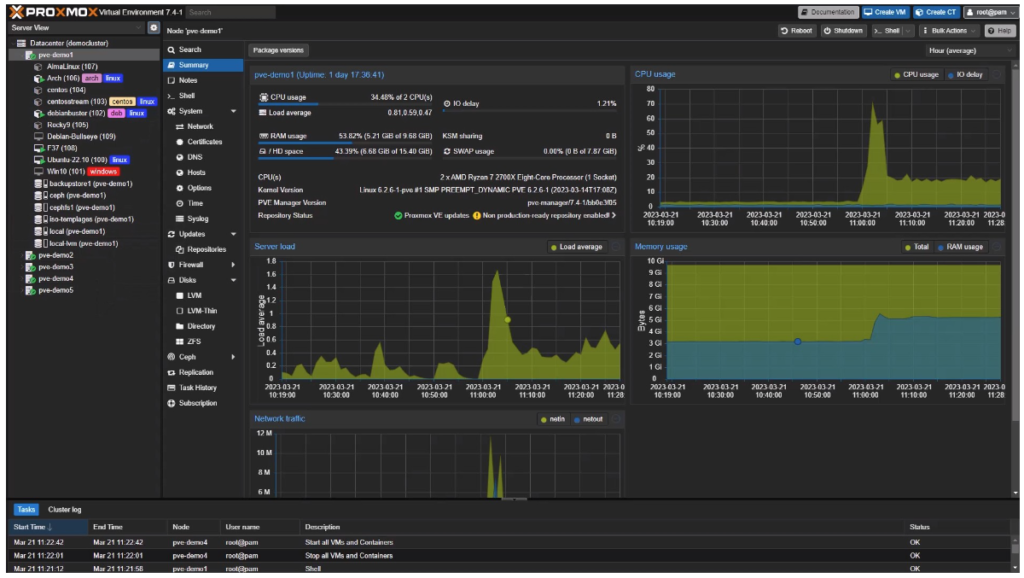
Proxmox VE, or Proxmox Virtual Environment, is a powerful platform for managing virtual machines (VMs) and containers. It offers a user-friendly interface and is known for its ease of installation and setup. Proxmox VE allows users to create and manage virtualized environments, making it a popular choice for hosting and managing virtualized systems.
One of the features of Proxmox VE is the use of Linux Containers (LXC), which provide lightweight, isolated environments for running applications. LXC allows users to run multiple Linux-based containers on a single host, providing a way to isolate applications and their dependencies while maximizing resource efficiency.
In the context of the recent incident involving unwanted cryptocurrency mining software appearing on a machine running qBittorrent, it’s possible that Proxmox VE and LXC were involved in some capacity. Without further details, it’s difficult to determine exactly how the cryptocurrency mining software ended up on the machine.
However, it’s worth noting that Proxmox VE itself is a secure and robust platform when properly configured and maintained. Like any software, it’s important to keep Proxmox VE and its components up to date with the latest security patches and updates to minimize the risk of security vulnerabilities.
In addition, users should exercise caution when installing third-party software and ensure that they only download and install applications from trusted sources. Unauthorized access and installation of cryptocurrency mining software can occur if the system is compromised due to weak security practices, such as using default credentials or failing to apply necessary security updates.
The incident involving the cryptocurrency mining software being installed on the Proxmox machine appears to be the result of a series of avoidable events rather than a sophisticated hacking attack. Here’s a breakdown of the sequence of events:
- Deployment of qBittorrent with Proxmox Helper Script: The user deployed a script, likely provided by tteck on GitHub, to install qBittorrent on their Proxmox Virtual Environment (VE) using Linux Containers (LXC). These helper scripts simplify the installation process, making it easy for users to install various software packages within LXC containers.
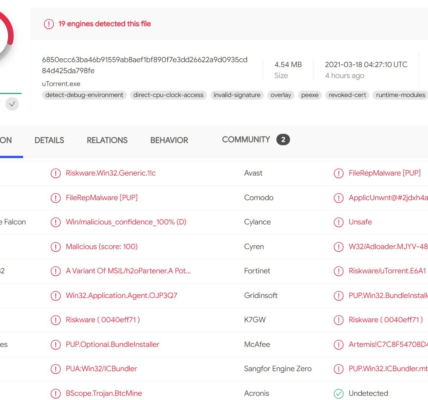
- Discovery of Cryptomining Software: Approximately a month later, the user noticed that their machine was exhibiting symptoms of heavy workload, indicating that cryptomining software (specifically xmrig) was running on their system. This software was mining Monero cryptocurrency, consuming system resources without the user’s consent.
- Removal of qBittorrent Script: In response to the discovery of the cryptomining software, tteck removed the qBittorrent LXC script as a precautionary measure. However, it was later determined that neither the Proxmox platform nor tteck’s script were directly responsible for the malware infection.
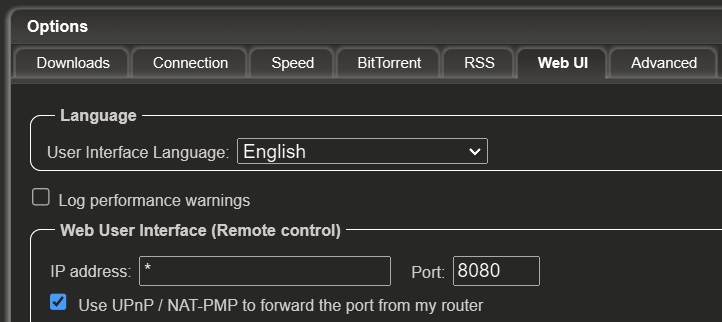
- Exposure of qBittorrent Web Interface: When qBittorrent is installed using the script and launched, it typically provides access to its web interface, which is accessible through web browsers. By default, qBittorrent uses port 8080 for its web interface, and to enable remote access, it may utilize UPnP (Universal Plug and Play) to automatically forward this port, thereby exposing the web interface to the internet.
The exposure of the qBittorrent web interface to the internet, combined with unchanged default credentials and possibly misconfigured UPnP settings, created a vulnerability that allowed an attacker to access the interface and install the cryptomining software without the user’s knowledge or consent.
To mitigate such risks, users should ensure they properly configure security settings surrounding qBittorrent’s web interface, including changing default credentials, disabling UPnP if not needed, and implementing additional security measures such as firewall rules to restrict access to the interface. Additionally, regularly updating software and promptly addressing security vulnerabilities can help prevent unauthorized access and malware infections.
Having this working in record time is all very nice, but that doesn’t mean it’s safe. To ensure that only the operator of the client can access the web interface, qBittorrent allows the user to configure a username and a password for authentication purposes.
This generally means that random passers-by will need to possess these credentials before being able to do damage. In this case, the default admin username and password were not changed and that allowed an attacker to easily access the web interface.
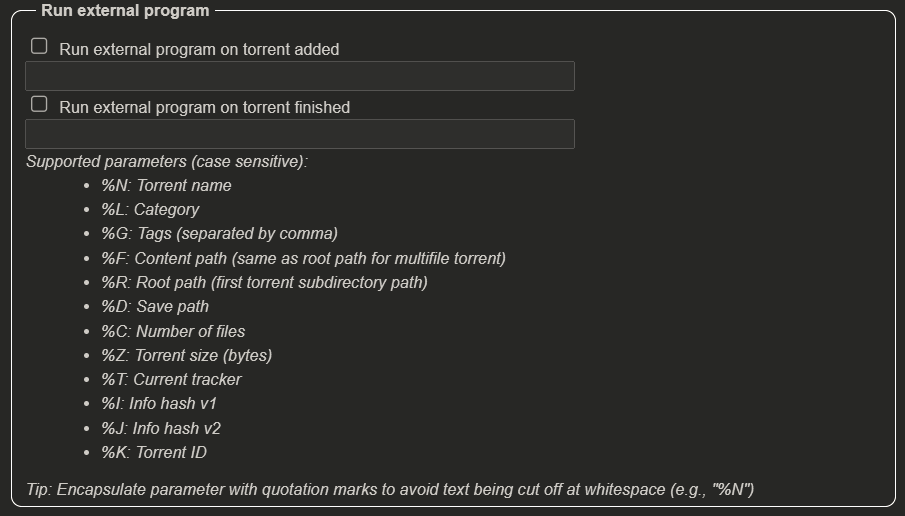
Attacker Told qBittorrent to Run an External Program
To allow users to automate various tasks related to downloading and organizing their files, qBittorrent has a feature that can automatically run an external program when a torrent is added and/or when a torrent is finished.
The options here are limited only by the imagination and skill of the user but unfortunately the same applies to any attacker with access to the client’s web interface.
The unauthorized cryptomining incident involving the qBittorrent client underscores the importance of implementing basic security measures to protect against such attacks. Here are some key takeaways from the incident:
- Change Default Credentials: The default admin username and password for qBittorrent (admin/adminadmin) are widely known and should be changed immediately after installation. By using unique and strong credentials, users can prevent unauthorized access to the web interface, even if it is exposed to the internet.
- Disable UPnP: qBittorrent often uses UPnP to automatically forward ports and expose its web interface to the internet. However, enabling UPnP without fully understanding its implications can create security vulnerabilities. Users should consider disabling UPnP in their routers unless absolutely necessary, as it can prevent unauthorized access to services and reduce the risk of exploitation.
- Understand Router Settings: Users should familiarize themselves with the settings and capabilities of their routers, including UPnP functionality. By understanding how their network operates and configuring their router securely, users can prevent unwanted exposure of services to the internet.
- Appreciate the Efforts of Script Developers: In this case, tteck, the developer of the Proxmox helper scripts, promptly responded to the incident by updating the default admin password and disabling UPnP in the qBittorrent LXC script. Users can benefit from the proactive measures taken by script developers to enhance security and protect against potential threats.
- Automate Installation Processes: Utilizing automated installation scripts for various software packages, such as Plex, Tautulli, Emby, and others, can save time and effort while ensuring consistent and secure installations. However, users should still review and customize the configurations to align with their security requirements.
By following these recommendations and maintaining vigilant security practices, users can mitigate the risks associated with torrent clients and other software installations, protecting their systems from unauthorized access and malicious activities.